7-Zip 是一款开源的解压缩软件,主要应用在微软 Windows 操作系统上。7-Zip 的作者曾在去年 3 月发布了首个针对 Linux 的官方版本,让 Linux 用户可以使用官方开发的 7-Zip 替换掉年久失修的 p7zip。
近日,研究人员 Kağan Çapar 在 7-Zip 中发现了一个漏洞,该漏洞可能导致黑客被赋予更高的权限以及执行任意指令。该漏洞的 CVE ID 为 CVE-2022-29072,漏洞影响 7-Zip 所有版本,其中也包括目前最新的 21.07 版本。7-Zip is an open source decompression software that is mainly used on Microsoft Windows operating systems. The author of 7-Zip released the first official version for Linux in March last year, allowing Linux users to replace the outdated p7zip with the officially developed 7-Zip.
Recently, researcher Ka?an ?apar discovered a vulnerability in 7-Zip that could allow hackers to be given elevated privileges and execute arbitrary commands. The CVE ID of the vulnerability is CVE-2022-29072, and the vulnerability affects all versions of 7-Zip, including the latest version 21.07.
To trigger the vulnerability is also very simple, the user only needs to drag the file with the .7z extension to the "Help > Content Area" of the 7-Zip software window, and the trigger method can be viewed in the GIF image below.
The vulnerability is due to a misconfiguration of 7z.dll and a stack overflow. After the software is installed, the files in the "Help > Content" area work through Windows HTML Helper, but after command injection, a subprocess will appear under 7zFM.exe. Due to the memory interaction in the 7z.dll file, the called out The cmd.exe child process is granted administrator mode.
The developers of 7-Zip have yet to provide a software update to fix the vulnerability, and it is unclear when 7-Zip will address the issue. 7-Zip was last updated in December 2021.
Temporary Workaround Although no official update has been provided to fix the vulnerability, the vulnerability is caused by the 7-zip.chm file contained in the installation folder, so the current workaround is to delete the affected file.
7-zip.chm is a help file that contains information on how to use and operate 7-Zip. Deleting this file does not result in a loss of functionality. After deletion, the help file will no longer open when the user selects Help > Content in the 7-Zip file manager or presses the F1 key on the keyboard.
In order to delete the file, the folder of the compression program must first be opened. Typically, this file can be found under C:\\Programs\\. After bringing up the "7-Zp" folder, the 7-zip.chm file can be deleted simply by right-clicking. In addition to deleting the 7-zip.chm file, users can also revoke write permissions for the 7-Zip program, allowing 7-Zip to only run and read files.
要想触发该漏洞也十分简单,用户只需将带有 .7z 扩展名的文件拖到 7-Zip 软件窗口的「帮助 > 内容区」,触发方式可以查看下方的 GIF 图。
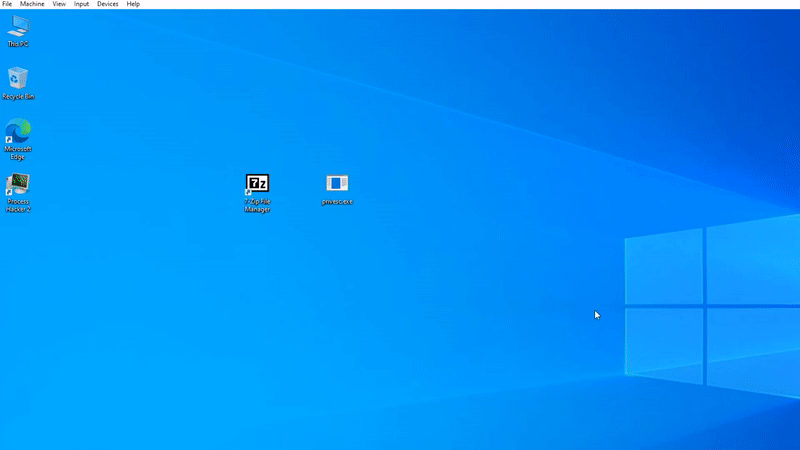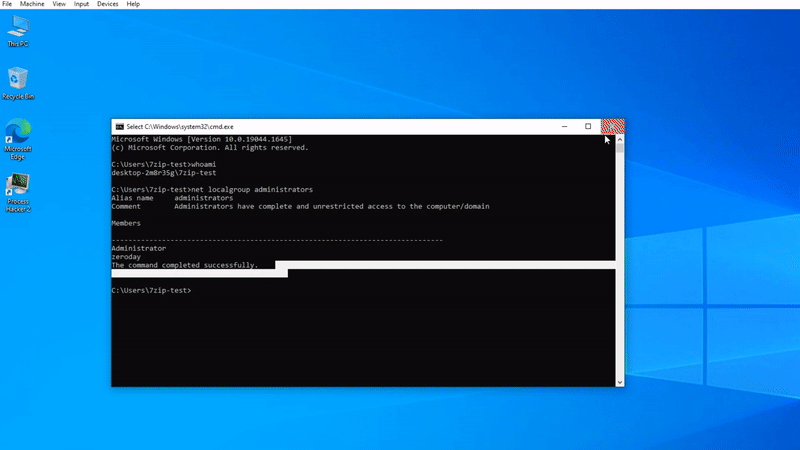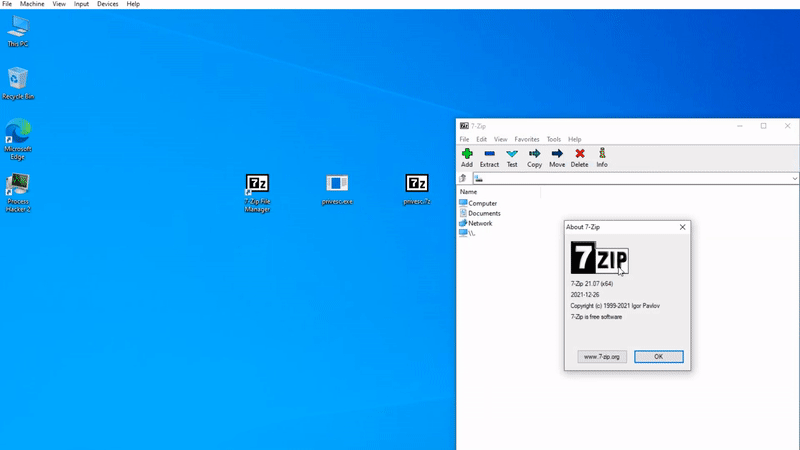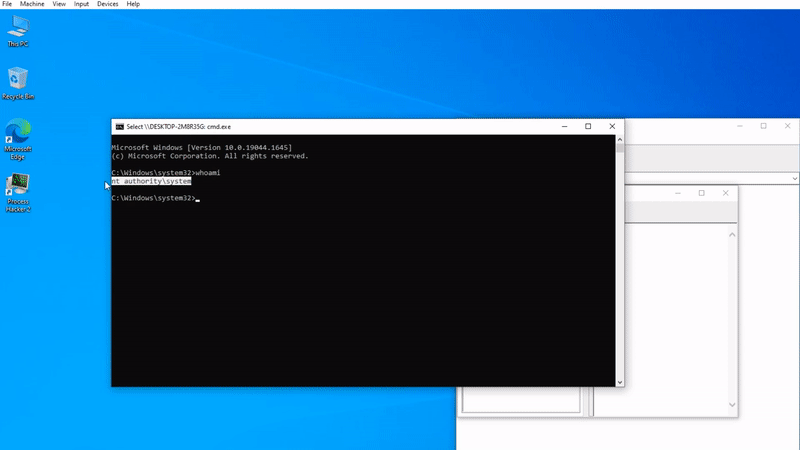
漏洞是由于 7z.dll 的错误配置和堆栈溢出所导致的。在软件安装后,「帮助 > 内容」区域中的文件通过 Windows HTML Helper 进行工作,但在进行命令注入后,7zFM.exe 下会出现一个子进程,由于 7z.dll 文件存在内存交互,调出的 cmd.exe 子进程会被授予管理员模式。
7-Zip 的开发者暂时还没提供软件更新来修复该漏洞,也尚不清楚 7-Zip 何时会解决该问题。7-Zip 最后一次更新还停留在 2021 年 12 月。
临时解决方法
虽然官方还没有提供更新来修复该漏洞,但该漏洞是由安装文件夹中包含的 7-zip.chm 文件所引起的,因此目前的临时解决方案就是删除这个受影响的文件。
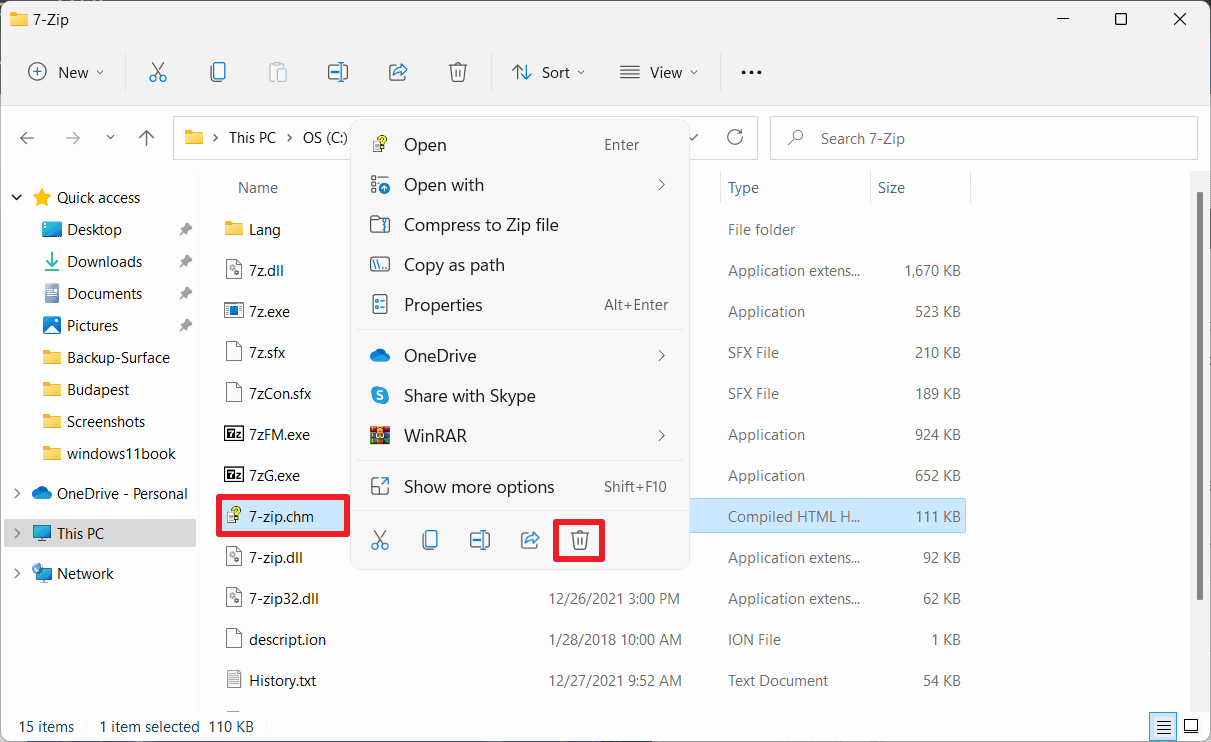
7-zip.chm 是一个帮助文件,包含关于如何使用和运作 7-Zip 的信息。删除该文件并不会导致功能缺失。删除后,当用户在 7-Zip 文件管理器中选择「帮助 > 内容」或按键盘上的 F1 键时,帮助文件将不再打开。
为了删除该文件,必须首先打开压缩程序的文件夹。一般情况下,该文件可以在 C:\\Programs\\ 下找到。调出 "7-Zp" 文件夹后,可以简单地通过右键点击删除 7-zip.chm 文件。除了删除 7-zip.chm 文件,用户还可以撤销 7-Zip 程序的写入权限,让 7-Zip 只能运行和读取文件。
