卡巴斯基修复四年老漏洞 注入HTML源码的唯一标识符会泄露用户隐私
多年来,卡巴斯基反病毒软件一直在各项安全测试中名列前茅。然而近日曝出的数据泄露事件,竟使得第三方能够长期监视用户的网络活动。德国网站 Heise.de 编辑 Ronald Eikenberg 指出,在其办公室电脑上的一个奇怪发现,让他知晓卡巴斯基反病毒软件造成了惊人的数据泄露。
(题图 via Heise.de)
作为 c't issue 3 / 2019 测试第一部分,小编会定期对反病毒软件进行测试,以观察其是否履行了企业所声称的安全承诺。
在刚开始的几周和几个月,事情似乎波澜不惊 —— 卡巴斯基软件的表现,与 WindowsDefender 基本相同或差强人意。
然而忽然有一天,Ronald Eikenberg 在查看了任意网站的 HTML 源码后发现,卡巴斯基竟然为其注入了如下代码:
<script type="text/javascript" src="https://gc.kis.v2.scr.kaspersky-labs.com/9344FDA7-AFDF-4BA0-A915-4D7EEB9A6615/main.js" charset="UTF-8"></script>
显然,浏览器正在加载来自 Kaspersky 域、名为 main.js 的外部 JavaScript脚本。尽管 JS 代码并不罕见,但当深入查看浏览器中显示的其它网站的 HTML 源码时,几乎都有同样奇怪的发现。
毫无意外的是,Ronald Eikenberg 竟然在个人网银网站上,也查看到了来自卡巴斯基的脚本。因此其断定 —— 这件事可能与卡巴斯基软件有些关联。
为了验证,Ronald Eikenberg 尝试了 Mozilla Firefox、Microsoft Edge、以及 Opera 浏览器,结果发现相同的代码随处可见。
鉴于没有安装可疑的浏览器扩展程序,他只能简单理解为是卡巴斯基反病毒软件在操纵当前的网络流量 —— 在未获得用户许可的情况下,卡巴斯基僭越了!
在此事曝光前,许多人可能只会在网银木马类恶意软件上观察到这种行为,以图窃取或篡改关键信息(比如悄悄地变更了网银转账的收款方)。现在的问题是 —— 卡巴斯基你到底在干嘛呢?!
经过对 main.js 脚本展开的一番分析,可知卡巴斯基会在判别某个‘干净’网站链接后,在地址栏显示带有谷歌搜索结果的绿色图标。
然而还有一个小细节 —— 加载卡巴斯基脚本的地址,也包含了一段可疑的字符串:
https://gc.kis.v2.scr.kaspersky-labs.com/9344FDA7-AFDF-4BA0-A915-4D7EEB9A6615/main.js
链接加粗部分,显然属于某种“通用唯一标识符”(UUID)。但是作为一款计算机安全软件,卡巴斯基要拿这串字符去识别或追踪谁呢?
扩展扩展验证,Ronald Eikenberg 在其它计算机上也安装了卡巴斯基软件,发现它确实会向其它系统同样注入 JavaScript 代码、并且留意到了一个至关重要的区别。源地址中的 UUID,在每台系统上都是不一样的。这些 ID 属于持久性的标识,即便过了几天也不会发生改变。显然,每台计算机都会拥有自己的永久分配 ID 。
而将这串 UUID 直接注入每个网站的 HTML 源码,绝对是一个糟糕头顶的主意。因为在网站域上下文环境中运行的其它脚本,都可以随时访问整个 HTML 源,甚至读取卡巴斯基这串 UUID 。
这意味着任何网站都可以读取并追踪卡巴斯基软件用户的网络 ID,只要另一个网站检测到了同一字符串,就能认定其访问源来自同一台计算机。基于这种假设,卡巴斯基显然是打造了一套危险的追踪机制,甚至比传统的 cookie 更加极端 —— 就算你切换了浏览器,也会被追踪并识别到在使用同一台设备、让浏览器的隐身模式形同虚设。
为避免更多用户陷入风险,c't 决定立即向卡巴斯基通报这一发现、并且迅速得到了对方的答复,称其已着手调查此事。
大约两周后,卡巴斯基莫斯科总部对这一案例进行了分析,并证实了 c't 的这一发现。该问题影响所有使用 Windows 版卡巴斯基安全软件的消费者版本,从入门机的免费版、互联网安全套装(KIS)、直至全面防护版(Total Security)。此外,卡巴斯基小企业安全版(Small OfficeSecurity)也受到了该问题的影响,导致数百万用户暴露于风险之中。
Heise.de 调查显示,卡巴斯基从 2015 年秋发布的“2016”系列版本中引入了该漏洞。但既然普通网友都能在无意间发现这个漏洞,包括营销机构在内的第三方,也极有可能早就展开了野外利用。
即便如此,卡巴斯基仍表示这种攻击过于复杂,因此发生的概率极低,对网络犯罪分子来说有些无利可图。然而 Heise.de 并不赞同该公司的说法,毕竟许多企业都在努力监视每一位网站来访者,这个持续四年的漏洞,很有可能是其展开间谍活动的一个福音。
万幸的是,在认识到事情的严重性之后,卡巴斯基终于听从了爆料者的要求,在上月发布了 CVE-2019-8286 安全公告,且相关补丁也已经打上。
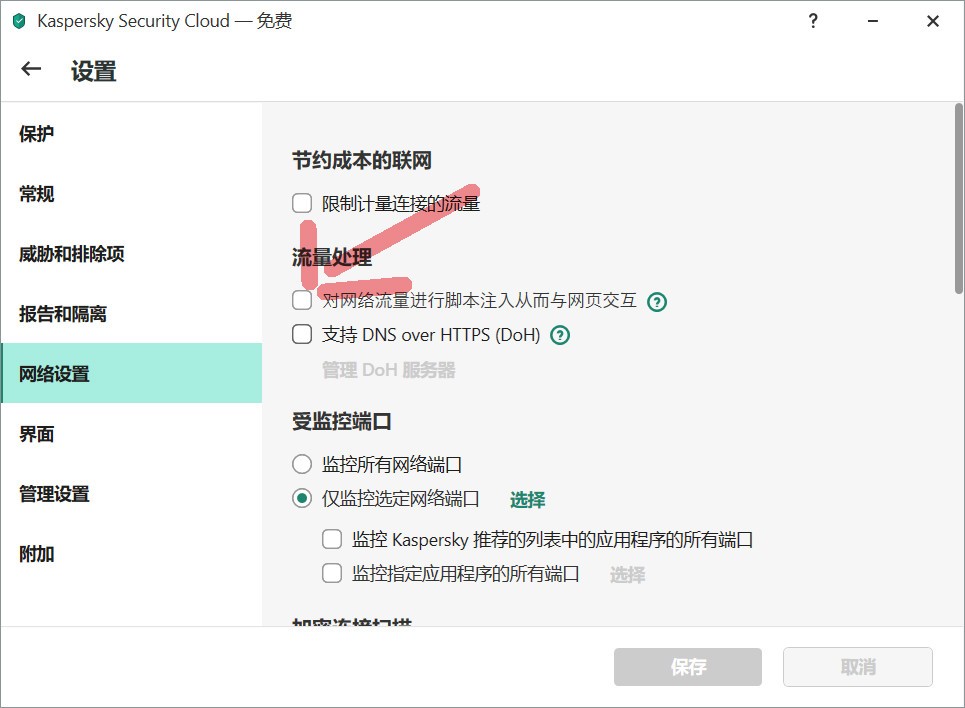
当然,为了安全起见,您也可禁用卡巴斯基软件中提供的相关功能:
点击主窗口左下角的齿轮(设置)图标 -> 点击‘其它 / 网络’-> 然后取消‘流量处理’下的‘将脚本注入 Web 流量以与网页交互’选项。
推荐
终身免费使用卡巴斯基Kaspersky Security Cloud 2021/2022 分享(含安装方法)百度网盘下载安装文件
Kaspersky Fixes Four-Year-Old Vulnerability Injecting Unique Identifiers into HTML Sources Can Reveal User Privacy For years, Kaspersky Anti-Virus has been among the best in various security tests. However, the recent data breaches have enabled third parties to monitor users' online activities for a long time. Ronald Eikenberg, editor of the German website Heise.de, points out that a strange discovery on his office computer made him aware of the staggering data breach caused by Kaspersky Anti-Virus.
(Title image via Heise.de)
As part 1 of our c't issue 3 / 2019 testing, we regularly test antivirus software to see if it lives up to the security promises the company claims.
In the first few weeks and months, things seemed to be smooth sailing—Kaspersky software performed roughly as well as Windows Defender.
However, one day, Ronald Eikenberg looked at the HTML source code of any website and found that Kaspersky had injected the following code into it: <script type="text/javascript" src="https://gc.kis.v2 .scr.kaspersky-labs.com/9344FDA7-AFDF-4BA0-A915-4D7EEB9A6615/main.js" charset="UTF-8"></script> Apparently, the browser is loading main.js from the Kaspersky domain external JavaScript script. While JS code isn't uncommon, it's almost always the same strange discovery when digging into the HTML source code of other websites displayed in the browser.
Unsurprisingly, Ronald Eikenberg even found a script from Kaspersky on his personal online banking website. So it concluded - this matter may have something to do with Kaspersky software.
To verify, Ronald Eikenberg tried Mozilla Firefox, Microsoft Edge, and Opera browsers and found the same code everywhere.
Given that no suspicious browser extensions are installed, he can only simply understand that Kaspersky Anti-Virus is manipulating the current network traffic - without the user's permission, Kaspersky has overstepped!
Before this came to light, many people may have only observed this behavior on online banking Trojan-like malware in an attempt to steal or tamper with key information (such as quietly changing the recipient of an online banking transfer). Now the question is - what the hell are you doing, Kaspersky? !
After some analysis of the main.js script, it can be seen that Kaspersky will display a green icon with Google search results in the address bar after identifying a "clean" website link.
However, there is a small detail - the address where Kaspersky scripts are loaded also contains a suspicious string: https://gc.kis.v2.scr.kaspersky-labs.com/9344FDA7-AFDF-4BA0-A915 The -4D7EEB9A6615/main.js link is in bold, apparently belonging to some kind of Universally Unique Identifier (UUID). But as a computer security software, who does Kaspersky want to use this string of characters to identify or track?
Extending Extended Validation, Ronald Eikenberg also installed Kaspersky on other computers, found that it did inject JavaScript code into other systems as well, and noticed a crucial difference. The UUID in the source address is different on each system. These IDs are persistent and do not change even after a few days. Obviously, each computer will have its own permanently assigned ID.
And injecting this string of UUIDs directly into the HTML source of each website is definitely a bad idea. Because other scripts running in the context of the website domain can access the entire HTML source at any time, and even read the UUID of Kaspersky.
This means that any website can read and track the network ID of a Kaspersky software user, and as long as another website detects the same string, it can assume that the source of the visit came from the same computer. Based on this assumption, Kaspersky has clearly created a dangerous tracking mechanism, even more extreme than traditional cookies - even if you switch browsers, you will be tracked and recognized that you are using the same device, allowing browsing The incognito mode of the device is useless.
In order to prevent more users from being at risk, c't decided to immediately notify Kaspersky of the discovery, and got a quick reply from the other party, saying that it had started to investigate the matter.
About two weeks later, Kaspersky's Moscow headquarters conducted an analysis of the case and confirmed c't's findings. The issue affects all consumer versions of Kaspersky Internet Security for Windows, from the free version for entry machines, Internet Security Suite (KIS), to Total Security. Additionally, Kaspersky Small Office Security was also affected by the issue, exposing millions of users to risk.
A Heise.de investigation revealed that Kaspersky introduced the vulnerability from the "2016" series of releases released in the fall of 2015. But since ordinary netizens can discover this vulnerability inadvertently, third parties, including marketing agencies, are likely to have already started exploiting it in the wild.
Even so, Kaspersky said the attack was too sophisticated and therefore unlikely to occur, making it somewhat unprofitable for cybercriminals. Heise.de, however, disagrees with the company's claims. After all, many companies are trying to monitor every website visitor, and this four-year-old vulnerability may well be a boon for its espionage.
Fortunately, after realizing the seriousness of the matter, Kaspersky finally obeyed the request of the whistleblower, and released the CVE-2019-8286 security bulletin last month, and the relevant patches have also been applied.
Of course, for security reasons, you can also disable the related functions provided in Kaspersky software: click the gear (settings) icon in the lower left corner of the main window -> click 'Other/Network' -> then uncheck the 'traffic handling' under ' Inject scripts into web traffic to interact with web pages' option.
It is recommended to use Kaspersky Security Cloud 2021/2022 for free for life. Share (including installation method) Baidu network disk to download and install files
